Windows Virtualization-Based Security: What is it?

Windows Virtualization-based Security (VBS) is a security integration that uses virtualization to enhance your device's security. It utilizes Windows hypervisor to create a virtual environment for security features to operate in isolated sections of the operating system.
With this feature, the trust boundaries of your computer are changed. It is not just trusting that every internal component (including the kernel) is safe. It's allowing segmentation to take place, utilizing hardware virtualization, to protect key system resources from being utilized in cyber attacks.
This protection helps defend against many attacks including:
- Kernel exploits - Ensuring only trust code can run in kernel mode
- Credential Theft - Protects against attacks that attempt to steal credentials from system memory
- Malware and Ransomware - Sophisticated malware and ransomware that uses kernel drivers and other advanced techniques.
- Direct Memory Access (DMA) Attacks - Requires all I/O devices capable of DMA to be behind an IOMMU, protecting against memory attacks.
There are many Windows security features that utilize the VBS feature:
- Processor Model-specific Register (MSR) Protection
- Windows Hypervisor constantly monitors and controls access to processor MSRs.
- This prevents malicious kernel code from misusing these registers to exploit the device.
- Memory Integrity
- Protects your system by ensuring that any code executed within the Windows kernel is trustworthy, using kernel mode code integrity checks in an isolated environment.
- Referred to as Hypervisor-protected Code Integrity (HVCI) or Hypervisor Enforced Code Integrity
- Application Guard (Being deprecated for Microsoft Edge for Business)
- Protects your device by running untrusted file and websites within an isolated Hyper-V enabled container.
- Credential Guard
- Protects authentication credentials by isolating NTLM hashes and Kerberos Ticket Granting Tickets (TGTs), ensuring only privileged system software has access.
- Helps prevent "pass the hash" and "pass the ticket" attacks.
- Hardware-Enforced Stack Protection
- Protects against Return-Oriented Programming (ROP) and Jump-Oriented Programming attacks.
There is a lot of controversy (a lot more than I thought there'd be) on whether you should enable this feature. As this feature segments off parts of the OS to better protect against many attacks, concerns about performance were introduced. The performance concerns I've seen mostly come from the PC gaming community saying that it affects certain games performances and should be permanently disabled. Since I haven't tested this theory, I can't entirely speak on the impact it has on gaming performance. In enterprise environments I have not seen any significant performance issues occur due to this feature being enabled and I recommend it to be enabled to better protect your device.
Requirements to Run Virtualization Based Security in Windows
- Windows Hypervisor Hardware support
- 64-bit CPU with Second Level Address Translation (SLAT)
- CPU support for virtualization extensions (Intel VT-X and AMD-v)
- IOMMU (Input-Output Memory Management Unit) or SMMU (System Memory Management Unit)
- DMA (Direct Memory Access) devices must be behind an IOMMU or a SMMU.
- Intel VT-D, AMD-Vi, Arm64 SMMU
- Trusted Platform Module (TPM 2.0)
- Firmware support for SMM Protection
- Unified Extensible Firmware Interface (UEFI)
- Memory Reporting
- UEFI v2.6 Memory Attributes Table (MAT)
- Secure Memory Overwrite Request (MOR) v2
- Secure Boot Enabled
- Memory Reporting
- Memory Integrity Compatible Drivers
Enable Virtualization-Based Security
This feature is enabled by default in Windows 10 and 11. But if you had it disabled in your environment, you can enable it using one of the following methods:
Method 1: Intune
My recommendation is to utilize Endpoint Security Baselines in Intune to enable this feature. You can do that by:
- Open Intune Admin Center and navigate to Endpoint Security > Security Baseline > Security Baseline for Windows 10 and later
- Select your current baseline (Create one if needed) and provide a name and description for it
- Under Configuration settings > Device Guard > Enable Virtualization Based Security
- Click Next and set your assignments (Always test policies on select devices before mass roll out)
- Review and save for the policy to be implemented.
You can also use Intune Configuration Policy to implement this as a single change which is almost identical to the steps above. Just instead of navigating to Endpoint Security, in the Intune Admin Portal you would go to Devices > Configuration > Policies and create the policy there.
Method 2: Group Policy
- Create a new group policy object using Group Policy Editor (gpedit.msc)
- Navigate to Computer Configuration > Administrative Templates > System > Device Guard
- Double-click on "Turn on Virtualization Based Security" and select "Enabled"
- Under Virtualization Based Protection of Code Integrity, select "Enabled without UEFI lock"
Check to see if Virtualization-Based Security is running
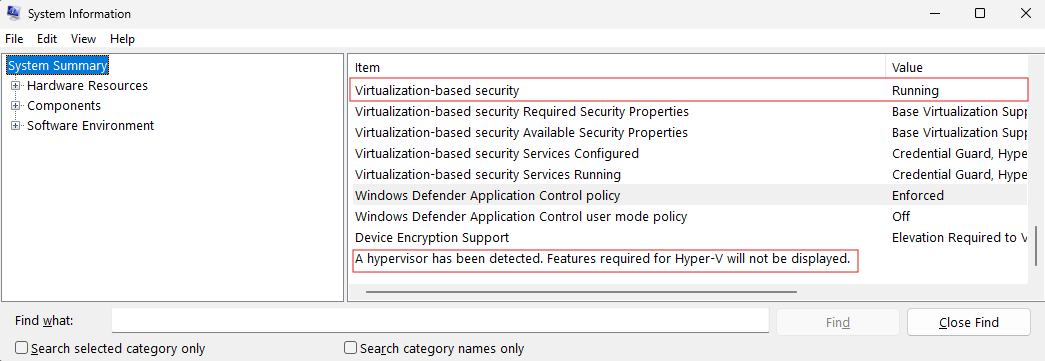
- Open start menu and search for and open "System Information"
- Under "System Summary" look for the item with "Virtualization-based security"
- This will say "running" when VBS is enabled.
References

