NetBIOS Vulnerability: Mitigating risks by disabling service

NetBIOS(Network Basic Input/Output System) is an old service that allows computers to communicate with each other over a LAN and to identify Windows systems names in TCP/IP. Originating in 1980s, NetBIOS ran over IEEE 802.2 and IPX using NetBIOS Frames (NBF) and NetBIOS over IPX/SPX (NBX) protocols. Today NetBIOS runs on NetBIOS over TCP/IP (NBT) protocol port 137 (Name Service), 138 (Diagram Service), and 139 (Session Service). There are many security concerns with NetBIOS and it is strongly recommended to have it disabled in production networks.
Vulnerabilities
As with most services that allow computers to talk to each other directly, vulnerabilities are introduced. Some of these vulnerabilities include:
- NetBIOS Name Service (NBNS) Spoofing - Attackers scan spoof NBNS responses to act as a Man-in-the-Middle and redirect traffic to malicious systems
- Microsoft Security Bulletin MS16-077 - Attacker can hijack network traffic or render untrusted content in a browser.
- Microsoft Security Bulletin MS03-034 - Allows attackers to receive random data from a target system's memory.
- Microsoft CVE-2017-0161 - NetBT doesn't maintain certain sequencing requirements, allowing an attacker to send specially crafted NetBT Session Service packets to the impacted system, where if successful, the attacker will be able to execute arbitrary code on the target.
Remediation
The recommended way to mitigate these vulnerabilities is to disable or block NetBIOS services when not required. These services should not be in use in majority of networks nowadays, but always double check your environment first before implementing this change.
Disabling NetBIOS Service via PowerShell Script
NetBIOS will need to be disabled on each network adapter. This can be done by running the following PowerShell script in an elevated PowerShell instance.
# Disable NetBIOS on all network adapters
Get-WmiObject Win32_NetworkAdapterConfiguration | ForEach-Object {
if ($_.TcpipNetbiosOptions -ne 2) {
$_.SetTcpipNetbios(2)
}
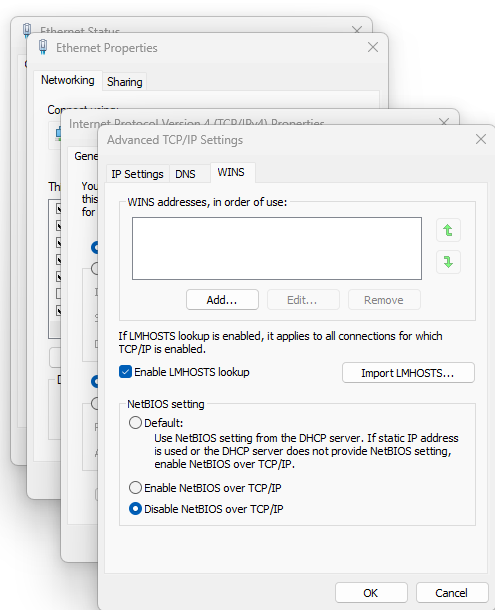
}You can validate the changes by going to Control Panel > Network and Sharing Center > Change Adapter Settings
Then find the adapter you want to verify has NetBIOS disabled and Right-click > Properties > Internet Protocol Version 4 (TCP/IPv4) > Properties > Advanced... > WINS. There is NetBIOS setting there and it should be set to Disable NetBIOS over TCP/IP.
Disabling NetBIOS on DHCP Server
Microsoft recommends disabling NetBIOS on DHCP servers where applicable as well. Follow their article for official support.
References
